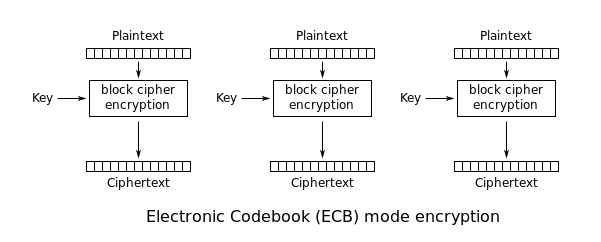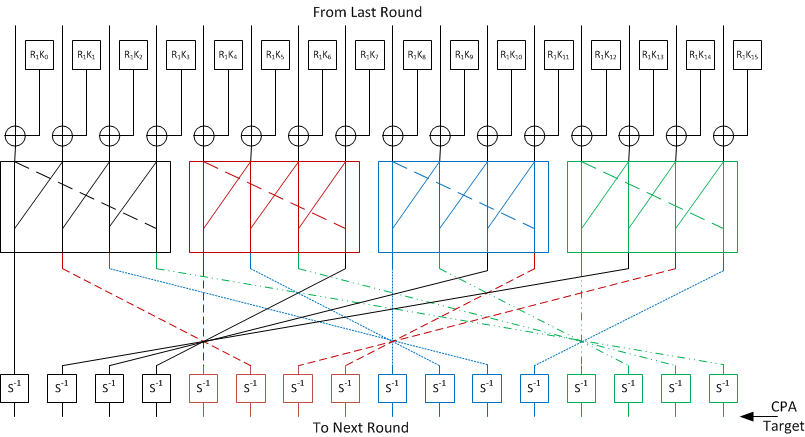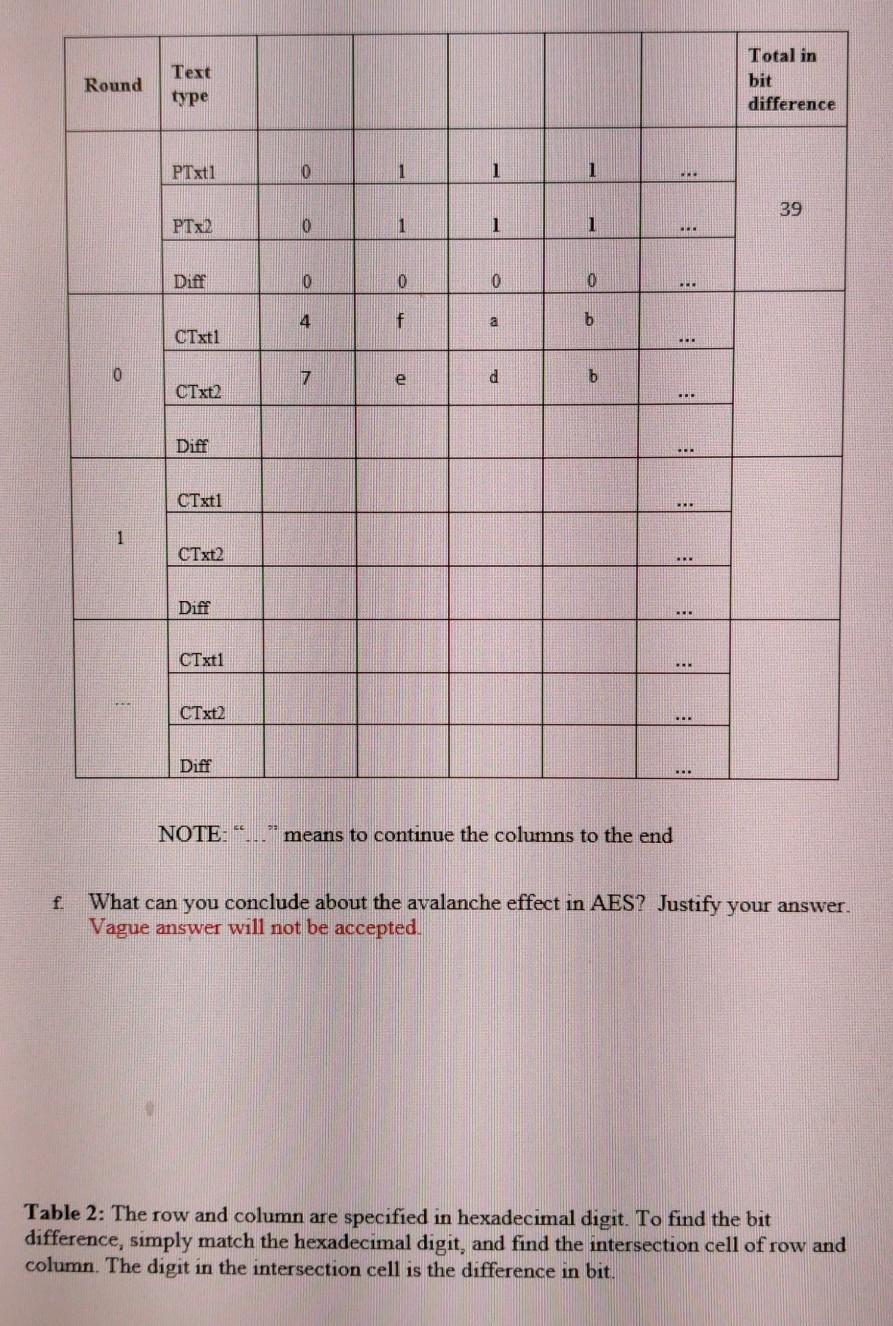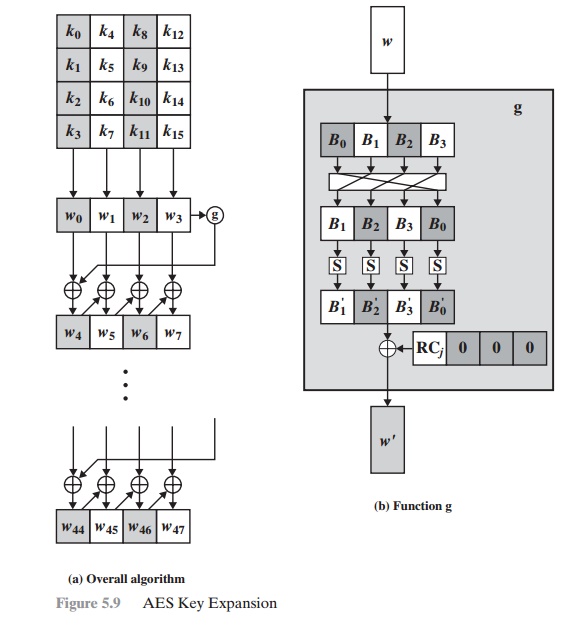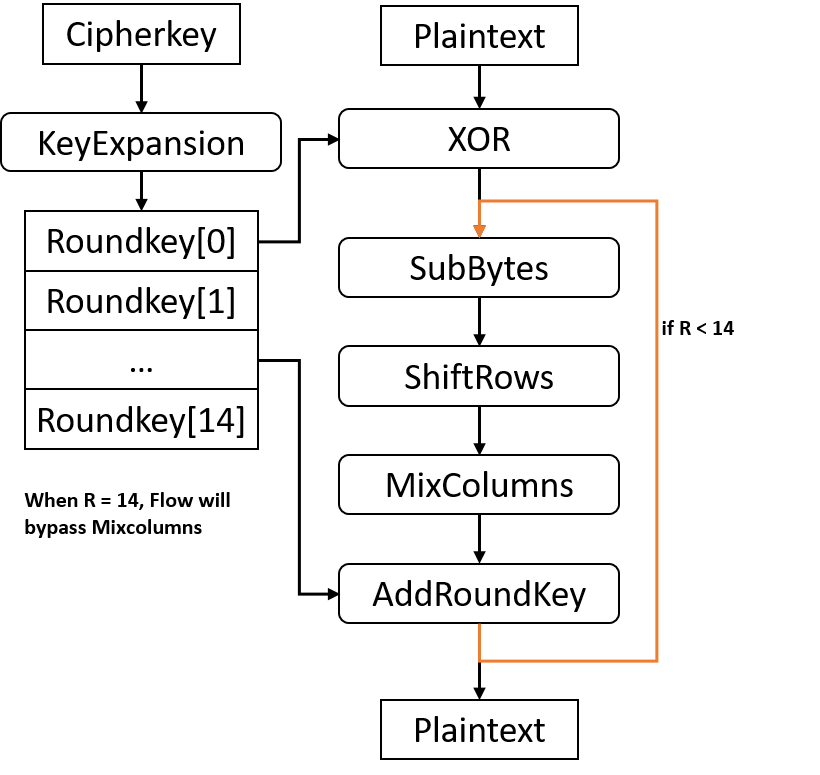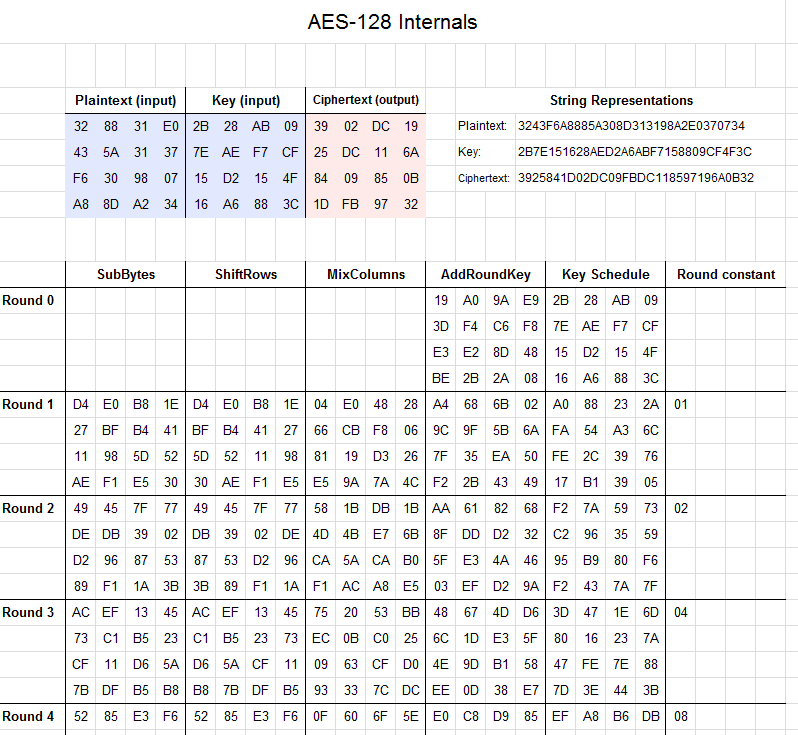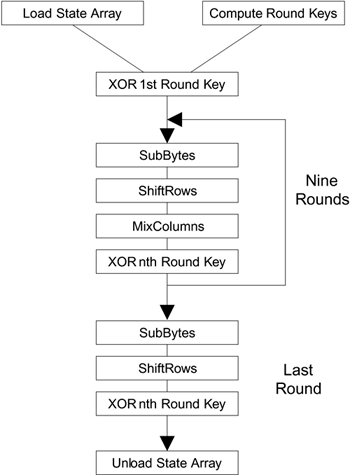
Steps in the AES Encryption Process :: Appendix A. Overview of the AES Block Cipher :: Appendixes :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org
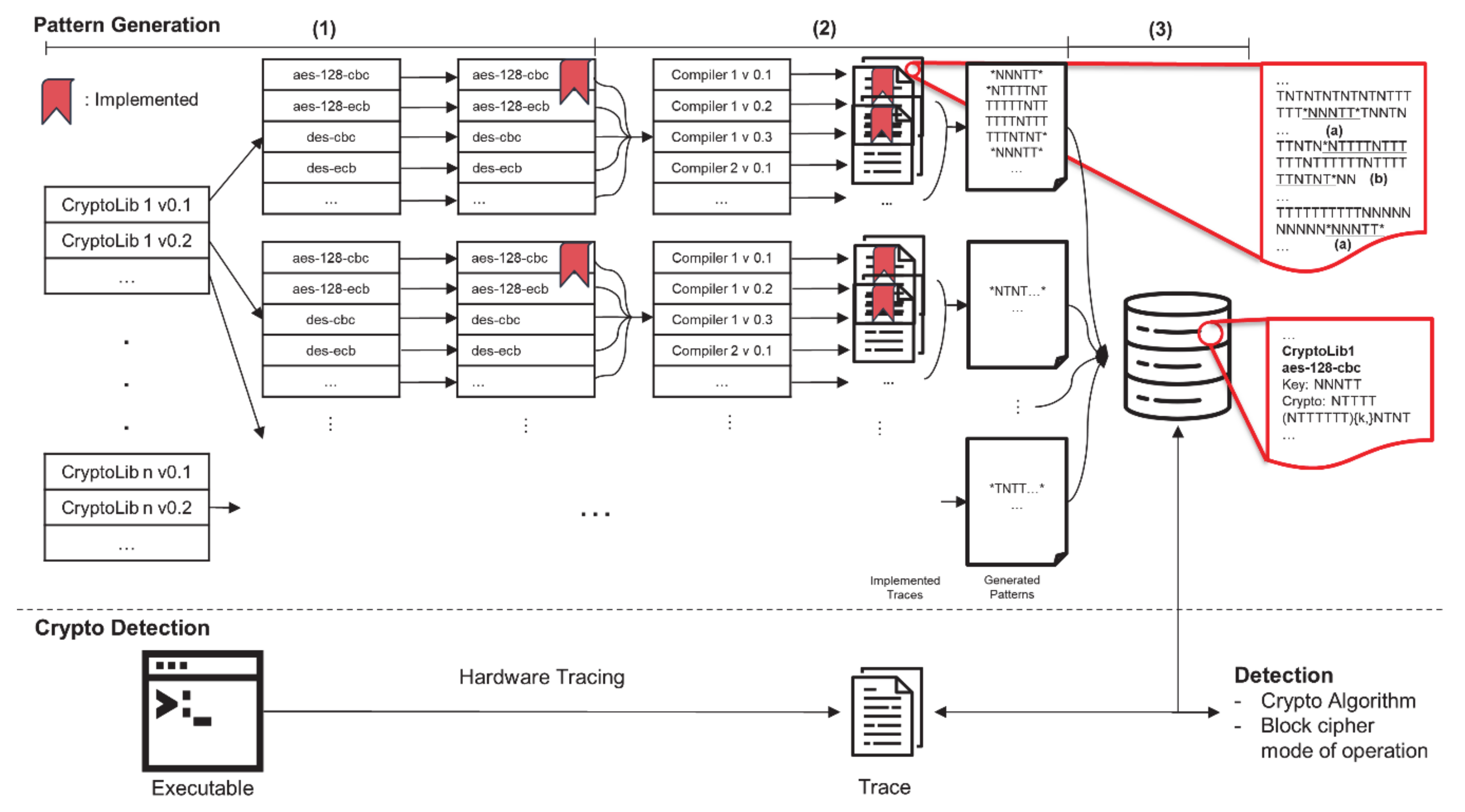
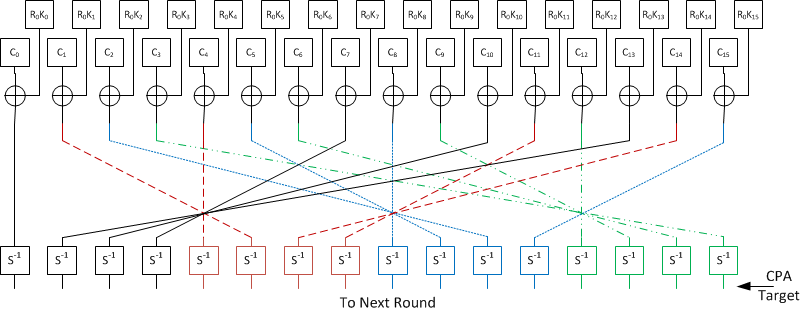
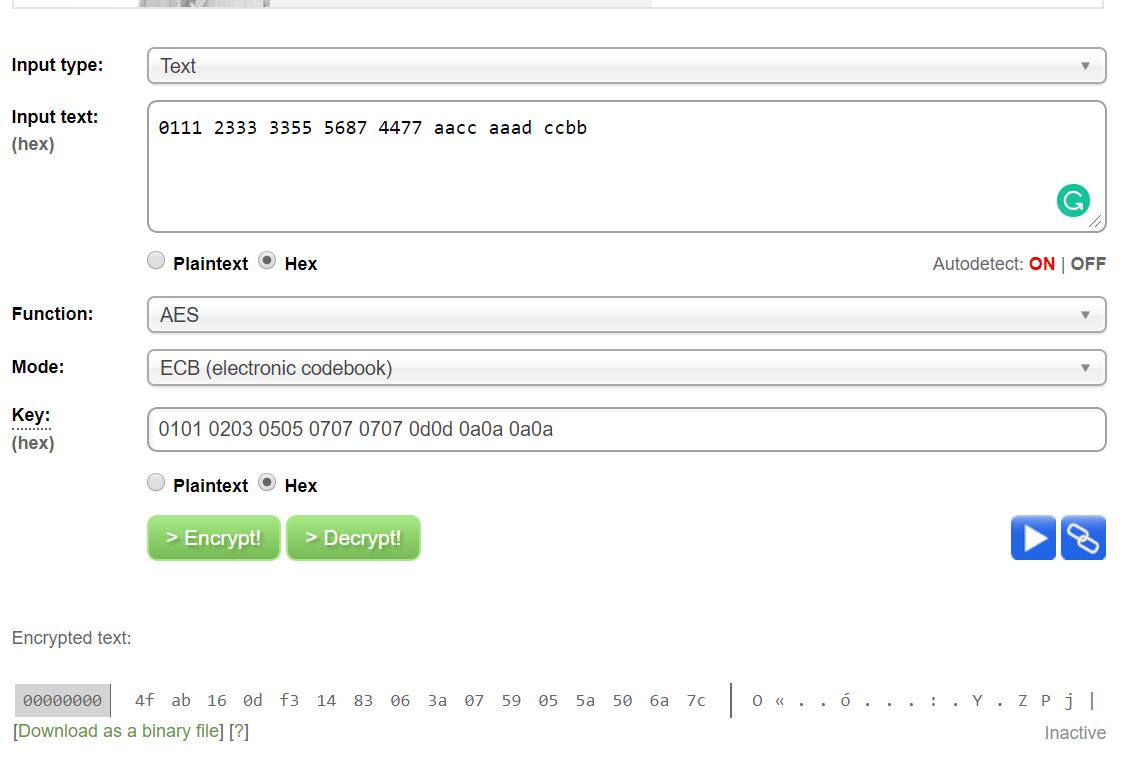
Electronics | Free Full-Text | Symmetric-Key Cryptographic Routine Detection in Anti-Reverse Engineered Binaries Using Hardware Tracing